Two thirds of FlashBack infected Macs running Snow Leopard

It is one thing for Apple to allow weeks to pass before issuing a patch for the BackDoor FlashBack trojan and quite another for the great majority of Mac users not to install it, which is apparently the current state of affairs.
Dr Web, the Russian security firm that outed the BackDoor FlashBack trojan and resulting botnet, is reporting that about two thirds of Macs infected are running some, likely out-of-date, version of Snow Leopard. They discovered this by poring over of the comm logs generated by 95,000 infected Macs.
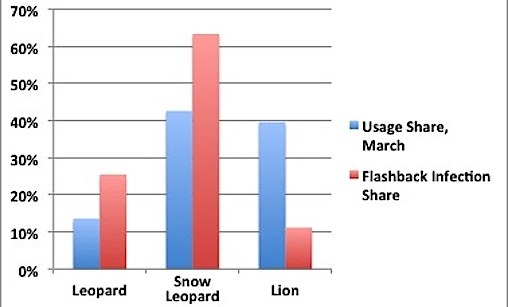
• 63.4 percent of the Flashback-infected machines were running OS X 10.6
— Snow Leopard runs on 46.8 percent of the Mac installed base• 25.5 percent of infect Macs were running OS X 10.5
— Leopard runs on 13.6 percent of Macs• 11.2 percent of those running Lion were infected
— 39.6 percent of all Macs run OS X 10.7
The salt in the wound here is that, regardless of the OS X version compromised, the leading cause of infection is simply that users aren’t applying the operating system, security and JAVA updates available from Apple. Well, duh.
“Qualys has seen some Microsoft updates be ignored by 20 to 30 percent of Windows PCs for four months or longer,” writes ComputerWorld. “But by Doctor Web’s data, Mac users are even less likely to update promptly, or even at all — OS X 10.6.7, the second-to-last update for Snow Leopard, was first issued 13 months ago, yet 9 percent of the infected Snow Leopard Macs run that version.”
Here’s the news — any computer (i.e. Windows, Linux, Mac) is only as safe as its user.
So, run Software Update and get the latest patches from Apple, and then get with the program. Securing your Mac takes little effort…
What’s your take?
Recent security posts:
— One-in-five Macs harbor PC viruses
— ClamXav 2.2.5: Tweaks Sentry, fixes auto-update issue
— FlashBack doom recedes for now
— Apple’s Java patch removes Flashback, but not all variants
— Apple lays Mac App, iTunes, iOS stores double authentication groundwork


Leave your response!